Governance
Governance
Ethical Management
Ethical Management Menu
Information Protection
SK Chemicals is committed to ensuring the safety and management of valuable information assets of customers and the company by introducing an abnormal sign monitoring system to prevent confidential data leaks. In 2023, the company obtained international standard information security certification (ISO 27001), establishing a global-level information security system.

Information Security Declaration
SK Chemicals aims to maximize the profits of each subsidiary through internal information protection to secure competitiveness and is committed to providing High-Quality Service through the protection of customer information.
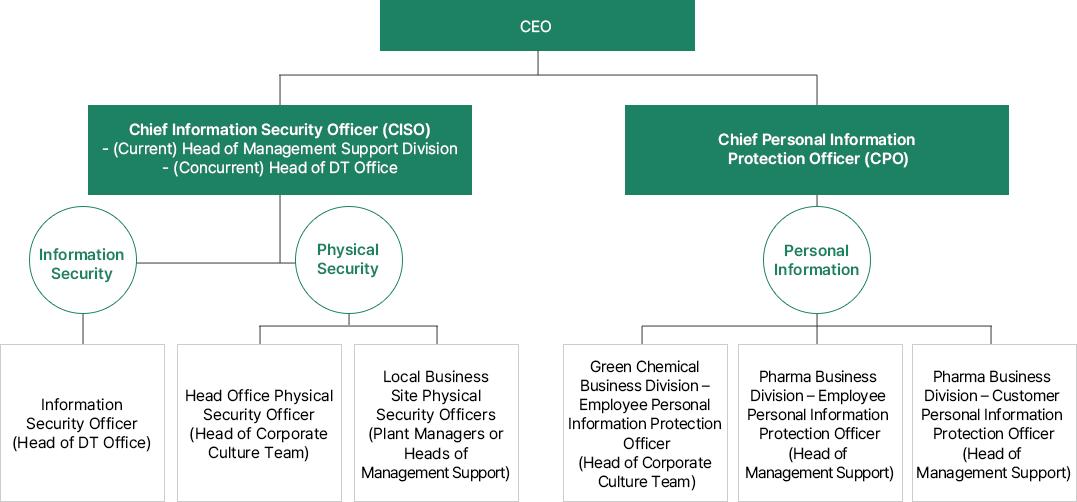
Information Security Management Organization
SK Chemicals designates the CEO as the Chief Information Security Officer (CISO) and supports the management (budget, personnel) of the security organization.
Standalone Whistleblower Channels
All stakeholders, including partners, customers, and other third parties, as well as SK Chemical's executives and employees, may report anonymously or in real names about SK Chemical's information security concerns. In addition, SK Chemicals guarantees strict protection, non-retaliation and confidentiality so that the informant does not suffer any disadvantages or discrimination due to the activities related to the report.
| Channel | Details |
|---|---|
| SK Chemical Webisite | https://skchemicals.com |
| esg_skchem@sk.com | |
| Phone | 02-2008-2008 |
